About Unified ID 2.0 (UID2)¶
Unified ID 2.0 (UID2) is an open-source framework that enables deterministic identity for advertising opportunities across the open internet for participants with access to the advertising ecosystem. UID2 is a standalone solution with a unique namespace and privacy controls that help participants meet local market requirements.
How UID2 works¶
Amperity may be configured as a UID2 Operator. A UID2 Operator is a participant in Unified ID 2.0 that is allowed to run the Operator Service. Operators may receive and store encryption keys and salts from the UID2 Core Service, salt and hash personal data to return raw UID2s, encrypt raw UID2s to generate UID2 tokens, and distribute UID2 token decryption keys.
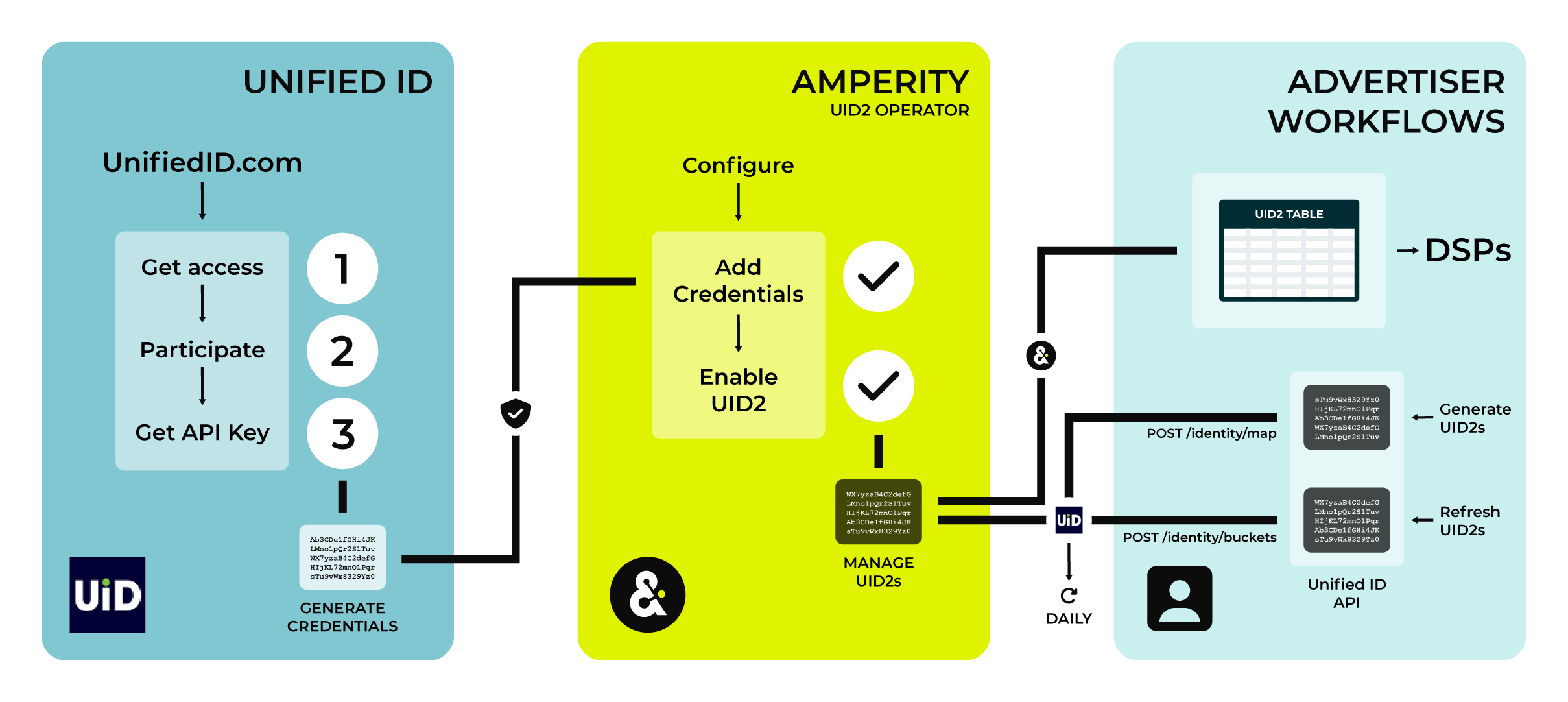
The following sections describe at a high level the series of steps that are required to configure Amperity to act as a UID2 Operator for your brand.

|
Before you can configure Amperity to act as a UID2 Operator for your brand you must do the following:
|

|
After your brand has adopted UID2 as part of your identity strategy you can configure Amperity to act as a UID2 Operator for your brand.
Use custom database tables, queries, and segments to configure Amperity to support your brand’s use cases for UID2. How does Amperity maintain UID2 tokens? Amperity uses the following UID2 endpoints when Amperity is configured to act as a UID2 Operator for your brand:
|

|
Build workflows against the UID2 table to support your brand’s UID2 workflows. Use custom database tables, queries, and segments in Amperity to build audiences of UID2 tokens that support your brand’s advertising strategies. Send these audiences to demand-side platforms (DSPs) that participate in Unified ID 2.0, such as The Trade Desk. DSPs can receive UID2s from advertisers as first- or third-party data. Advertisers buy impressions across a range of publisher sites. DSPs help advertisers decide which ad impressions to purchase and how much to bid on them. |
Prerequisites¶
Before your brand can configure Amperity to generate UID2 tokens you must do the following:
Agree to a UID2 participation policy, which is a legal requirement for UID2 sharing.
Get an API key. Use the credentials for this API key to allow Amperity to access endpoints in the UID2 API and act as a UID2 Operator for your brand.
Get access to UID2¶
To get access to the UID2 framework, you may sign up directly from the Unified ID 2.0 website or connect directly with your The Trade Desk representative (or UID2 administrator).
Participate in UID2¶
You must agree to a UID2 participation policy, which is a requirement for UID2 sharing .
Important
Talk with your The Trade Desk representative if you are unsure of which participation policy is required to support your brand’s UID2 use cases.
Get Mapper credentials¶
Each participant in UID2 has its own set of unique Mapper credentials , which allow access to specific areas within the UID2 ecosystem.
To configure Amperity to act as a UID2 Operator for your brand you must be a Mapper participant in Unified ID 2.0.
A mapper participant is a broad category that includes advertisers , data providers , data on-boarders, measurement providers, identity graph providers, third-party data providers, and any other organization that sends data to other participants and organizations that collect user data and push it to other UID2 participants.
Important
Use your brand’s Mapper participant credentials to configure Amperity to act as a UID2 Operator.
Configure Amperity¶
After your brand has adopted UID2 as part of your identity strategy you can configure Amperity to act as a UID2 Operator for your brand.
Add the UID2 table to your brand’s database.
Add Mapper credentials¶
Add credential to Credentials tab in Settings.
Add your brand’s Mapper credentials for UID2 to Amperity. Open the Settings page, select the Credentials tab, and then click Add credential.
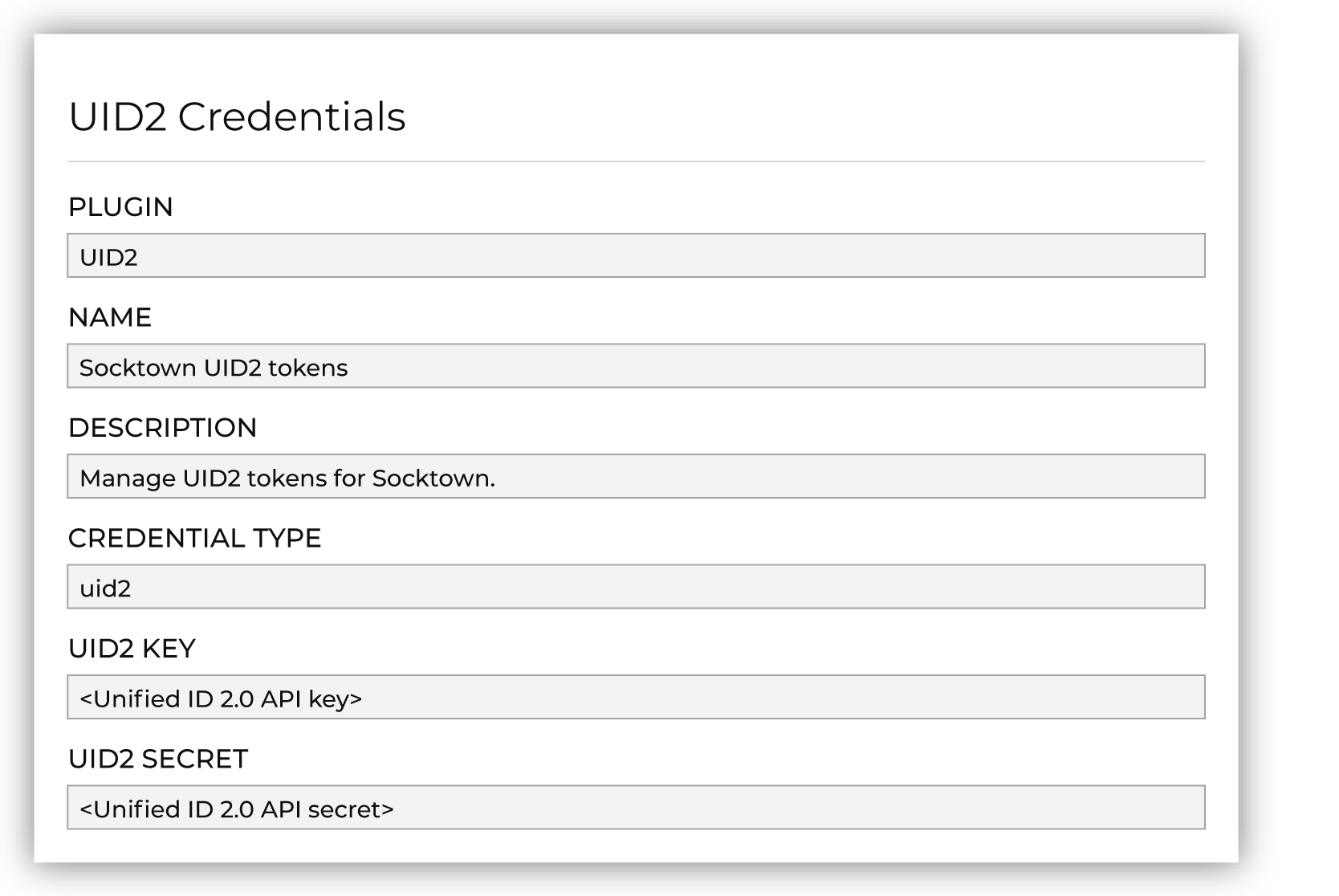
Choose the UID2 plugin. Provide a name and description for the credential that ensures users within your tenant know it is related to UID2. Add the API key and the client secret for your brand’s Mapper participant credentials.
Enable UID2 token generation¶
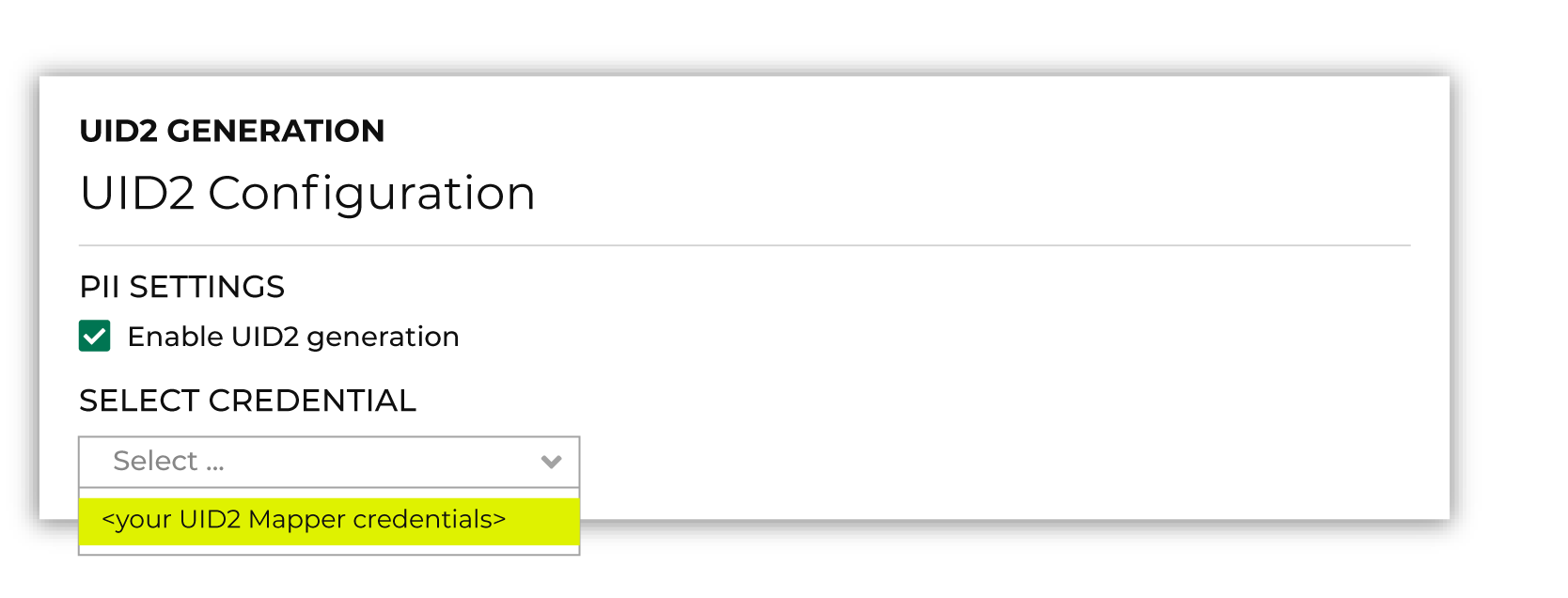
UID2 token generation is enabled from the Customer 360 page. Click the UID2 link to open the UID2 Generation dialog box. Select the Enable UID2 generation checkbox, and then choose your brand’s Mapper credentials from the Select credentials dropdown.
Add UID2 table to database¶
Add the UID2 table to any database as a passthrough table. The UID2 table is a core table.
The UID2 table has the following columns:
Column name |
Data type |
Description |
|---|---|---|
Bucket ID |
String |
A unique identifier for the salt bucket used to ensure that expired UID2 tokens are refreshed. This value is returned in the response from the POST /identity/map endpoint. Note Each UID2 token is associated with a salt bucket that links that token to a specific point in time. Salt buckets expire. Approximately 1/365th of all salt buckets are rotated daily. Amperity monitors salt buckets on a daily basis to determine which UID2 tokens need to be refreshed. |
String |
The email address for the customer. Amperity gets this value from the email field in the Unified Coalesced table. |
|
Normalized Email |
String |
The normalized email address sent from Amperity to the POST /identity/map endpoint for mapping. This value is returned in the response from the POST /identity/map endpoint. |
UID2 |
String |
The raw UID2 value for the customer. This value, when encrypted, may be used as a UID2 token. This value is returned in the response from the POST /identity/map endpoint. |
About UID2 workflows¶
Use custom database tables, queries, and segments in Amperity to build audiences of UID2 tokens that support your brand’s advertising strategies. Send these audiences to demand-side platforms (DSPs) that participate in Unified ID 2.0, such as The Trade Desk.
DSPs can receive UID2s from advertisers as first- or third-party data. Advertisers buy impressions across a range of publisher sites. DSPs help advertisers decide which ad impressions to purchase and how much to bid on them.

|
Advertising with UID2 enables the use of use first-party data to build omnichannel campaigns across devices using a single identifier. Using UID2 as part of your advertising strategy will help your brand:
|

|
Data providers can use UID2 to enable the use of third-party data . This approach to advertising can reduce identity fragmentation and connect third-party data to a more durable, omnichannel, cross-device identifier. |